This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies Find out more here
Admin
Last seen: 6 months ago
Comprehensive tutorials and guides on Linux, Windows, software applications, and useful shortcuts. Enhance your technical skills with step-by-step instructions and expert tips
Top 25 command in ubuntu linux
Discover the top 25 most useful and powerful command line tools in Ubuntu Linux to enhance your productivity and efficiency.
Top 25 command in fedora linux
Discover the top 25 essential commands for Fedora Linux users, from navigating the file system to managing processes and networkin...
Top 25 command in rhel linux
Discover the top 25 essential commands for RHEL Linux, including powerful tools for managing files, processes, networking, and sys...
Windows 11 Not Booting
Experiencing issues with Windows 11 not booting? Find solutions and troubleshooting tips to get your system up and running smoothl...
Bypassing TPM and Secure Boot Checks for...
Learn how to bypass TPM and Secure Boot checks for Windows 11 with this comprehensive guide. Get your system up and running withou...
Secure Boot Not Enabled for Windows 11
Secure Boot Not Enabled in Windows 11? Learn how to turn on Secure Boot to enhance system security and protect against malware thr...
TPM 2.0 Not Detected in Windows 11
Facing TPM 2.0 not detected issue in Windows 11? Learn how to troubleshoot and fix the problem quickly to ensure smooth system per...
Windows 11 Compatibility Check Issue
Experiencing issues with Windows 11 compatibility check? Get solutions to resolve the problem and ensure smooth upgrade process.
Windows 11 Upgrade Failed
Facing issues with the Windows 11 upgrade? Learn why your Windows 11 upgrade failed and how to troubleshoot the installation proce...
Common Windows 11 Issues and How to Fix
Encountering problems with Windows 11? Get solutions and troubleshooting tips for common issues with the latest operating system.
How to Download Windows 11 ISO
Learn how to easily download Windows 11 ISO file for free with step-by-step instructions. Upgrade to the latest operating system t...
How to Check Windows 11 Compatibility
Learn how to check Windows 11 compatibility on your device in a few simple steps. Ensure your system meets the requirements for a ...
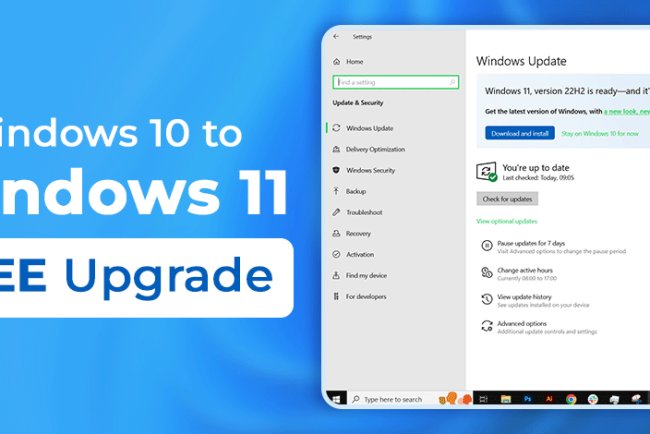
How to Upgrade to Windows 11
Learn how to upgrade to Windows 11 with step-by-step instructions and tips to ensure a smooth transition to the latest operating s...
How to Install Windows 11
Learn how to install Windows 11 on your PC with step-by-step instructions and tips to successfully upgrade your operating system.
How do you list all open ports in CentOS...
Learn how to list all open ports in CentOS using various commands such as netstat, ss, and nmap in this comprehensive guide.
How do you check the status of the firew...
Learn how to check the status of the firewall in CentOS using simple commands. Ensure your system is secure and protected with thi...
How do you close a specific port in Cent...
Learn how to effectively close a specific port in your CentOS firewall to enhance security and protect your system from potential ...
How do you open a specific port in CentO...
Learn how to open a specific port in CentOS firewall by following these step-by-step instructions. Keep your system secure while a...
How to Install and Configure Apache on D...
Learn how to install and configure Apache web server on Debian operating system with step-by-step instructions and screenshots.
How to Install Debian Step-by-Step?
Learn how to install Debian step-by-step with this comprehensive guide. Follow the instructions to set up Debian on your system ha...
How do you disable a service from starti...
Learn how to disable a service from starting at boot in CentOS by following simple steps and managing your system efficiently.
How do you enable a service to start at ...
Learn how to enable a service to start at boot in CentOS by following simple steps. Ensure your services run automatically every t...
How do you stop a service in CentOS?
Learn how to stop a service in CentOS by using the systemctl command, ensuring proper shutdown and management of services on your ...
How do you start a service in CentOS?
Learn how to start a service in CentOS with step-by-step instructions, including enabling, starting, and stopping services for opt...
How do you check the status of a service...
Learn how to use the systemctl command to check the status of a service in CentOS and troubleshoot any issues quickly and efficien...